Code injection
Code injection
hi guys am going to solve PentesterLab Code injection if you dont know about code injection it's one of big bugs that let hacker to execute codes in server i will give link explain all information about this bug now let us begin in this section include four task and how to get RCE and execute php code .
this first challenge let pwn it
pentesters try to get error simple way to add double quotes
oh nice you can see it's use eval ,eval one of function in php that when you pass string it convert it to php code now we get error let try to understand how it work here
if you see in second picture it's expecting ! and if you compare it with first one you can see !!! if you change name in parameter it's still add !!! to end
after reversing code i can write simple code act like this
now we have simple code now let to try to fix error
if you add "." it fix error and now error here now explain what means this payload
eval("hacker"." ") it balanced string as we know . in php it concatenation between string now add payload ".phpinfo();"
eval("hacker ".phpinfo();" ") it will work
boom yah you pwned it
now we go to crack second challenge
ah this time it's using id to sort some record now go to fuzzing it
cool we get some error now you notice usort() expects parameter 2
after googling about usort and how it's work now i can make some reversing here
first to make correct reversing i doing some simple code to help me to balanced
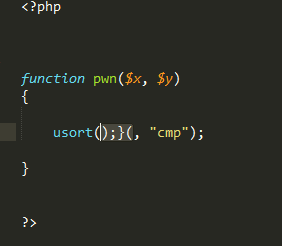
now let work to get pwn
if we enter );} to usort
); close usort function and } it's close the pwn function and add comment // to comment reset of the code
finally payload will be );}[but php here]//
oh yah pwned it
now go to challenge 3
ammmmm here some regex now this regex it have pattern it /lamer/ and content it's hello lammer and new it's means replace as you can see it's replace lammer with hacker now how we can pwn it ??
after googling and read about regex in php it reveal some issue with regex here
when you using /e it's new value as PHP code, before performing the replace it
now we can pwn it
here payload new=phpinfo()&pattern=/lamer/e&base=Hello%20lamer
it's replace phpinfo with lammer before do that it's execute php because we add /e to pattern
pwn it now i will give nice trick this challenge it's replace content with value and echo it ok
if use ` ` with echo in linux you get shell in box yah if echo `id`; it will execute it as linux command
now navigate to last challenge
now fuzzing it and get error
cool this error reveal what we need to pwn server assert it's php function it assert — Checks if assertion is FALSE in this case it just print now you can notice assert(): Failure evaluating code: 'hacker'' now you can see there additional ' that generate this error now i will make simple code can that help us to reversing and pwn it
now let balanced it
if we enter hacker'.phpinfo().'
we balanced it now copy this payload and execute it on server
oh yah pwn it
we pwned all four challenge now i will make some links that can help you to understand it
Code injection [https://www.owasp.org/index.php/Code_Injection]
eval [http://php.net/manual/en/function.eval.php]
usort [http://php.net/manual/en/function.usort.php]
regex [http://php.net/manual/en/function.preg-replace.php]
assert [http://php.net/manual/en/function.assert.php]




















Comments
Post a Comment